Cyber Security Governance as a Service will help you with your strategic goals and objectives.
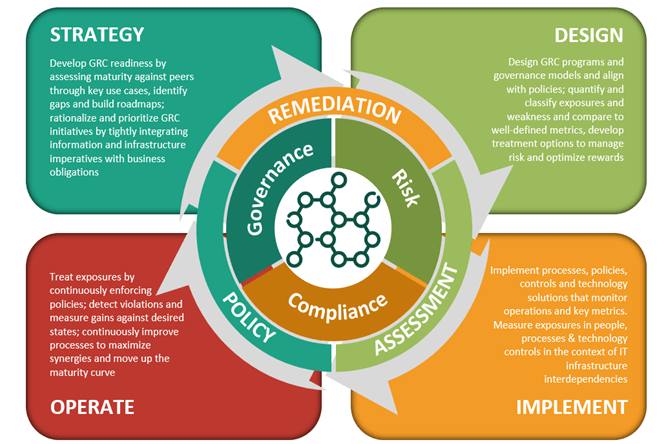
Cyber security is a strategic enterprise risk that goes far beyond information technology. The growing cyber space has brought along a series of advantages as well as disadvantages for your business. A proper security policy framework and computer architecture will protect your business and data from possible cybersecurity issues. A weak system exposes your entire computer architecture and resources to cyber-attacks and compromises which can easily bring your business to a halt if no proper cybersecurity governance policies exist. Cyber security governance is the sets of systems by which out team will help your business direct and take control of IT security.
A Cyber Maturity Assessment will give your organisation an in-depth look at your cybersecurity issues
Our Cyber Security Governance as a service team will use a Cyber Maturity Assessment to address your business needs. A Cyber Maturity Assessment will give your organization an in-depth analysis of your businesses’ cybersecurity issues which shows how your business is able to protect is resources and information assets against any threats. The analysis also adds on information regarding the preparedness of your business towards handling such threats when they occur. Our cyber maturity assessment takes a very holistic approach to issues regarding cybersecurity and includes the critical steps that will make your computer systems up to the levels and prevent security threats.
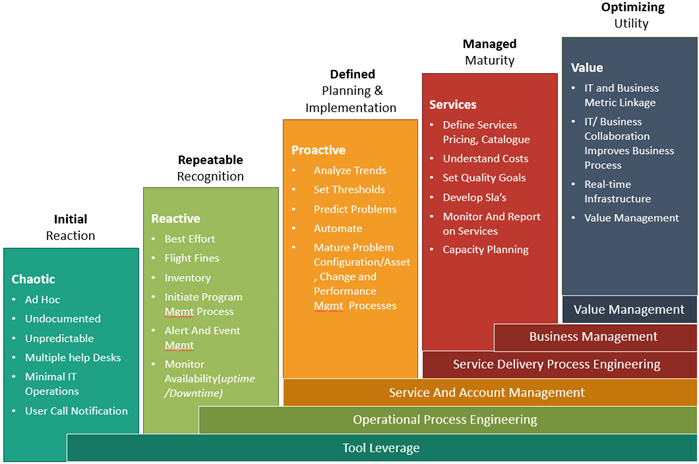
In the assessment, we consider the people involved in your businesses’ cyber security governance, the processes which occur within the business and the technology and resources used to achieve it.
Benefits
All-Round: We will perform an extensive Cyber Security Maturity Assessment to investigate all the Cyber Security Governance issues to improve your business.
Experience: our CISO’s are highly experienced and can quickly understand the business needs and can make an immediate impact, being productive from the outset.
Robust: Zenosec will provide you with a needs analysis to identify all security policies, processes and compliance to stay in line with Cyber Security Governance expectations.
Cost: Zenosec can provide the Cyber Security Governance as a Service to meet your budgetary needs.
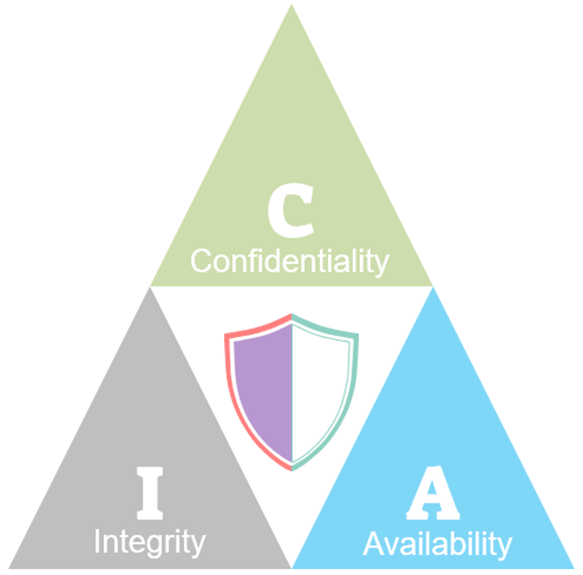
Confidentiality
We begin by assessing the security programs which can be used to inform the entire cyber security governance principles and policies. Confidentiality is the main principle which informs the necessary security measures to protect your organizations abilities to protect the data, assure the security of objects and the businesses resources. Confidentiality principles in the maturity model will assess the needs for the business in protecting your data as it is being stored, processed and while in transit. These key issues must be addressed in the security plan for the business to specifically affect all the concerns and security issues which might be used to attack the business and its systems.
Integrity
This second component of the Cyber Maturity Assessment plan will address all relevant issues which deal with the security, consistency, and accuracy of data over a period of time. This principle in the assessment is very hard to achieve for most businesses yet it poses very dire risks to the entire systems. Integrity
in the systems means the systems observe measures and policies which makes data be trustworthy, accurate, and very highly consistent with all the needs of the business. This principle will help your business know the relevant tools and security options to prevent any malicious modifications, deletions or access to protected data.
Availability
Your business needs data to inform the business operations and strategic ideas to achieve targets and visions. For this, the availability principle in the assessment will help you identify all the tools and necessary controls to make your business achieve the high availability need for your data. With this service, we analyze the needs of your business and inform you of all the necessary hardware and software components that will support your business in achieving strategic objectives. This feature will be enough to make a business gain significant competitive advantage as data can be used to inform very key business decisions easily and faster.
Trusted Adviser
Cyber security demands attention not only from the chief information officer – but also from the rest of the C-Suite, the board and, indeed, employees and business partners throughout the organization.
ZENOSEC knows that to deliver cyber security value, businesses must first determine the appropriate levels of acceptable and tolerated risk. We assist you understand how best to align your information protection agenda to your dynamic business and compliance priorities. By focusing on security needs versus wants, ZENOSEC teams build enterprise-wide security strategies that help to move organizations from reacting in crisis mode to having a proactive, value-added business solution. ZENOSEC’s practice offers customer tailored services.
A powerful cyber security strategy should align to the business vision, objectives and innovation projects. If implemented effectively, it can enhance product integrity, customer experience, operations, regulatory compliance, brand reputation, investor confidence and more – leading to a return on your cyber investments.
Download our Security Governance as a Service white Paper Download

