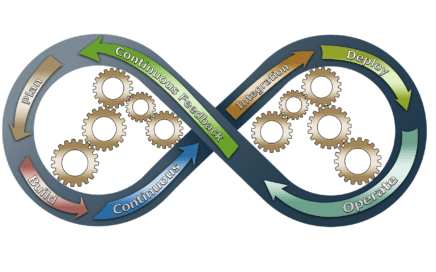
BYOD security tips to minimize risks
The practice of BYOD is extremely beneficial for the large as well as small businesses. This practice helps the organization to create a hazel-free working environment. Though BYOD possesses several advantages, it is recommended that an organization should take appropriate steps before implementing it to their business. This will helps […]